Enforce FinOps Tags Before Code Is Deployed
New feature announcement: FinOps tags can now be checked directly in the engineering workflow in CI/CD, before anything goes to production, by shifting them left. Both the key and value can be verified. If the tagging policy has not been followed, the engineer will be notified and the code pull request can be blocked until it is fixed.
Tagging challenges
One of the first tasks assigned to the FinOps teams is to determine “who is using what” – that is, which teams, business units, products, etc. are spending the most on cloud. To accomplish this, they use tags. Tags are labels that all cloud resources should have and are key-value pairs. For example, a server could be tagged with: product=HackerNews, environment=production, team=blueTeam. Without proper tagging, it becomes difficult to track resource usage effectively, especially across multiple cloud providers.
However, FinOps teams face challenges because all tools available are reactive. These tools begin by analyzing cloud bills and providing visibility of tags from there. This means that they are looking at resources that are already running in production and costing money. A customer recently shared, “I want all resources to be properly tagged. But if they are not, I would rather a resource not be tagged at all than be tagged incorrectly.”
Shift FinOps tags left
That was our “aha” moment! FinOps teams can define a tagging policy that can be validated in CI/CD before resources are launched. This is important because if code is shipped with the wrong tags, FinOps teams will have to fight for sprint time to fix them. Even if you shut down an untagged resource directly in the cloud, the next time Terraform runs, the resource will launch again with no tags. You need to fix the issue at its root.

I’m very excited to announce that Infracost will now check for both your tag keys and allowed values directly in the engineering workflow before the code is merged to go to production. This results in two big benefits:
- No more untagged or mis-tagged resources in your cloud bills. Infracost will check both key and values, as well as typos and upper/lower case issues, and make sure they are fixed.
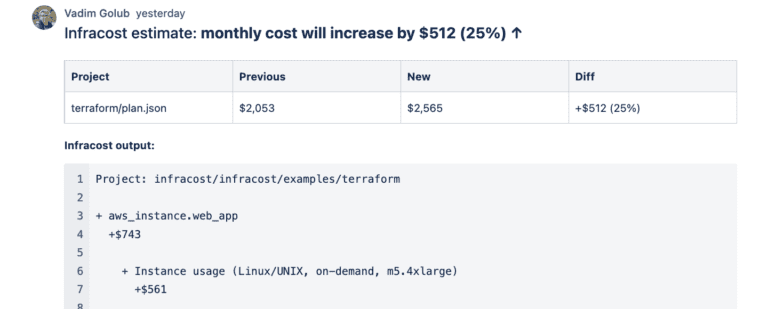
- Save engineering time. The engineers are told directly in their code which resources are not tagged properly, and exactly which lines of code to edit to fix the issue (shown below). Even if you are using AWS Service Control Policies or Azure Policies, this will be beneficial as these tools fail the deployment pipeline (not the build), meaning the engineer will need to change the code again and open more pull requests, and have their code re-reviewed before they can deploy again.
This is what your engineers will see when they open a pull request to change infrastrcutre:

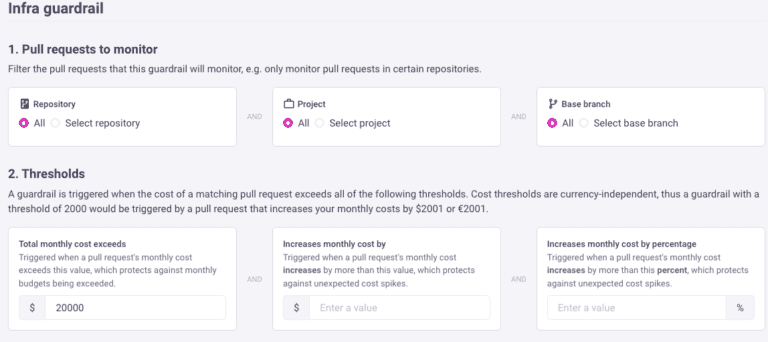
In addition to fixing FinOps tags and being proactive, Infracost also provides tracking of conformity over time. Once you connect Infracost to your GitHub or GitLab and set your tagging policies, it will display all the resources that are complying and not complying with your tagging policies. These results are tracked over time, so you can monitor progress directly from the code (shown below).

Get started now
This feature is now live for AWS, Microsoft Azure and Google Cloud (GCP). Connect to your GitHub or GitLab environment – define your tagging policies and immediately see the results.
If you’d like to see a live demo of Infracost, email me at hello@infracost.io
Thanks,
Hassan and the Infracost team 👍🏽
Making FinOps proactive