New Cost Policies: Catch Mistakes And Budget-Breaking Changes in CI
Cost policy checks are now reported directly inside pull request comments! Native integration with Open Policy Agent simplifies writing policies that are checked before resources are launched.
I love shipping fast! And to ship fast, as engineers we usually automate things:
- unit tests quickly tell me if my change broke something.
- linting tools quickly tell me about obvious errors and coding standard mishaps.
- security scanning tools quickly tell me if there are potential issues in my code.
The key benefit of these guardrails is that they fit into my workflow and tell me something I didn’t know. And I like that because the earlier I know about issues, the easier they are to fix.
Cost policies enable you to do the same with cloud costs; engineering teams need confidence to ship fast without slowing down to check things manually, for example:
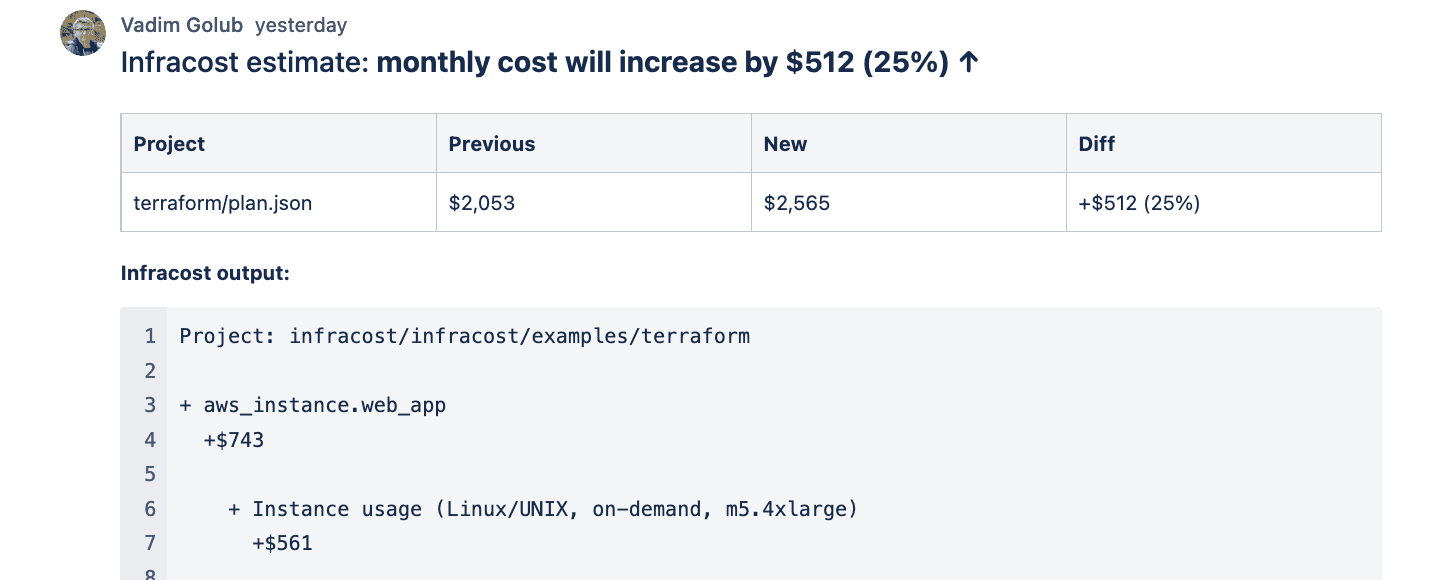
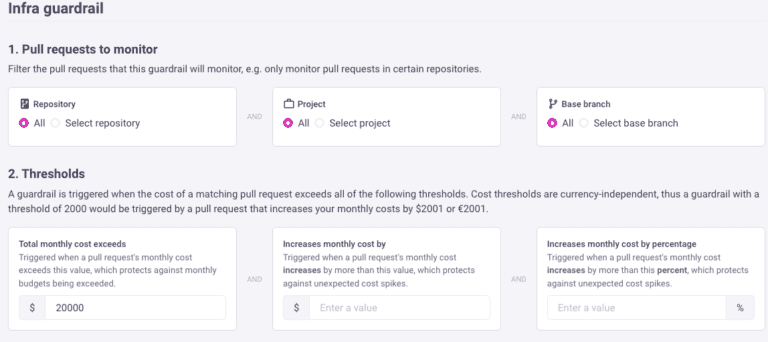
- Am I making any mistakes? Many users have told us about cases when they saw an unexpected cost estimate when using Infracost. There are 3 million price points between AWS, Azure and Google; it’s easy to make mistakes with this amount of complexity. Just like unit tests, policies enable you to write your own pass or fail checks. For example, if a pull request increases the cost estimate by $1000, add a note so I review it in details; 80% of the time, this won’t kick-in so I ship fast with confidence, I’m looking to flag that 20%.
Back in January we announced integration with various policy engines like Open Policy Agent (OPA) and HashiCorp Sentinel. That enabled teams to write policies but the integration was not easy and the output was hidden in CI/CD logs.
Today we’re excited to release Infracost v0.9.20 that includes native integration with OPA! You can now evaluate cost policies written in OPA’s policy language (Rego) directly through the Infracost CLI, and see the output inside pull request comments.
Check out the following video for a guided tour of this new feature and read our docs to get started. Contribute to this GitHub issue if you have feedback about the policy behaviors.