New FinOps Policies & tfsec Creators Join Infracost
Happy July!
We’re excited to share a key insight from the recent FinOpsX conference: FinOps has shifted left 🚀 This approach, which we’ve championed since 2021, integrates cloud costs and best practices into the development workflow before deployment. Our new ebook explains how shifting left saves engineering time and prevents cost overruns—check it out!

Improved Pull Request Comments
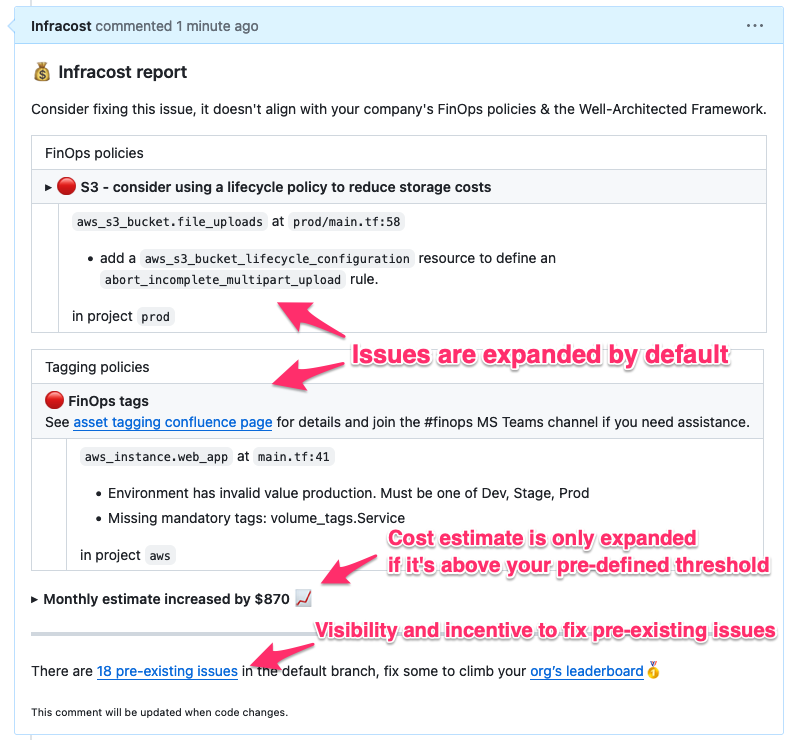
After many usability tests, we’ve released an improved pull request comment format for Infracost Cloud users where:
- FinOps and tagging policy issues are expanded by default, making it easy for engineers to see the recommendations quickly.
- The cost estimate is only expanded if it’s above your budget guardrails.
- There is a link to all pre-existing tagging and FinOps issues in the repo being changed and an incentive for engineers to fix them.
The Infracost GitHub and GitLab apps have already been switched to the new format, CI/CD users should upgrade to the latest CLI version to get the new format. Please reply to this email and let me know what you think about the new format!
New FinOps Policies
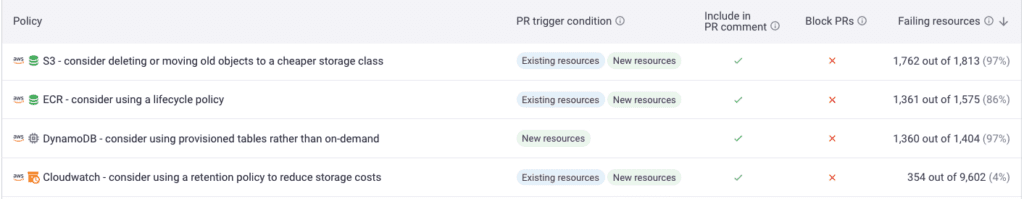
We constantly review the Well-Architected Frameworks and speak to FinOps practitioners to automate best practices – we added 12 new FinOps policies last month. This enables engineers to keep focused on delivery, leaving Infracost to check and warn them when a better option exists, which include:
- AWS Graviton for RDS, including Aurora, ElastiCache, and OpenSearch – Graviton instances are 20% cheaper than equivalent x86 instances!
- AWS ECR – consider using a lifecycle policy
- AWS DynamoDB – consider using provisioned tables rather than on-demand
- AWS DynamoDB – consider using TTL on tables
- Google Compute – Consider using predefined machine types
- AWS, Azure, and Google – consider using preferred instance types, which you can define to standardize around certain instance families for improved Savings Plans or Reserved Instance discounts.
Check the Infracost Cloud > Governance > FinOps policies page to see if your repos are following the new recommendations.
Use Low CO2 Regions
Do you know which cloud regions are low CO2? For example, Google’s europe-west1-3 regions are low CO2, but europe-west4 is not. In many cases, enterprises want to encourage their engineers to use specific cloud regions and sometimes enforce that. For example, some Infracost customers want to encourage low CO2 Google Cloud regions, and others want to only allow certain Azure regions due to compliance or latency reasons.
We’ve released a new FinOps policy to simplify this, so engineers don’t need to read lengthy docs or remember these things when they write infra-as-code. You just enter the regions you want to encourage, a custom message to explain why, and whether pull requests that fail the policy should be blocked. That’s it – it takes 1min to set up from the Infracost Cloud > Governance > FinOps policies page.
Only Trigger Policies When New Resources Are Added
By default, FinOps policies trigger when existing resources are changed, or new resources are added. However, for policies where changing an existing resource could require downtime or have other deployment implications, you can now change the policy to only trigger when new resources are added. This option is also useful for FinOps teams at large enterprises who prefer to roll out policies slowly across thousands of code repositories and hundreds of engineering teams.
Creators of tfsec have joined Infracost
Finally, I’m thrilled to announce that Owen and Liam, the creators of the incredibly popular tfsec open-source project, have joined Infracost! They bring a wealth of experience from the security space and parsing infra-as-code to our team 🚀